I’m not sure when it clicked for you that tilt shift could be had easily and practically, in camera with some recent models, but that time was today for me.
Tilt–shift photography is the use of camera movements that change the orientation and/or position of the lens with respect to the film or image sensor on cameras.
Sometimes the term is used when the large depth of field is simulated with digital post-processing; the name may derive from a perspective control lens (or tilt–shift lens) normally required when the effect is produced optically.
“Tilt–shift” encompasses two different types of movements: rotation of the lens plane relative to the image plane, called tilt, and movement of the lens parallel to the image plane, called shift.
Tilt is used to control the orientation of the plane of focus (PoF), and hence the part of an image that appears sharp; it makes use of the Scheimpflug principle. Shift is used to adjust the position of the subject in the image area without moving the camera back; this is often helpful in avoiding the convergence of parallel lines, as when photographing tall buildings.
Tilt-shift photography, Wikipedia
The only mainstream lens manufacturer I know of that sells tilt-shift lenses is Canon. While I like Canon cameras and love the capabilities of tilt-shift lenses, I would like to see if there are other ways to handle this issue. It’s somewhat of a niche problem, but it’s one that’s worth addressing.

And then it dawned on me. Some camera models have sophisticated 5-axis image stabilization. That means they effectively tilt and shift the sensor, along with “shake it all about” and so on, in order to keep a longer exposure clear. But what if we were to modify the firmare, to introduce a special section in the camera menus, where the vertical and horizontal angles at which the sensor is kept when facing a scene could be manually adjusted through that special section? We could effectively introduce optical tilt and shift capabilities by manipulating the sensor, while still using the same lenses.
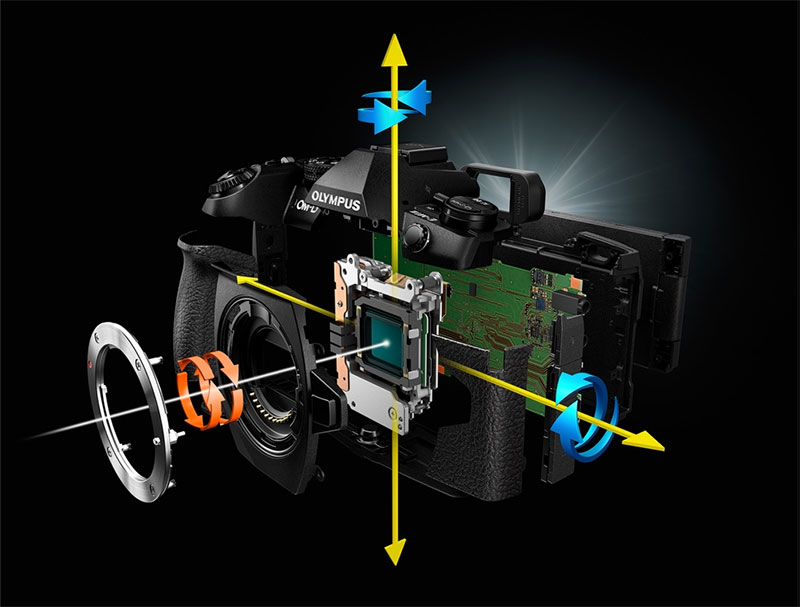
Lightroom offers some options to tilt and shift the image after it’s been taken, but any good photographer will tell you it’s better to capture the image you need directly in camera. Introducing a special menu that lets us tilt and shift the sensor, perhaps using the buttons and dials already built on the camera, would provide this valuable niche capability to those who do not own Canon tilt-shift lenses and do not shoot with Canon cameras. It’d literally be a bonus firmware upgrade that could be pushed out and the new feature should just work. There would be some limitations in the amount of movement, since the IBIS engine wasn’t originally built for this, but it would work, and in future iterations of the IBIS, I’m sure it would work even better.
If you liked this idea and you work in product design and development, you may want to have a look at my consulting website.















































